catchme is the rootkit/stealth malware scanner that scans for:
catchme can also delete, destroy and collect malicious files.
How to scan
How to delete malware files
To delete malicious files on the "Script" tab paste the list after "Files to delete:" command and click the "Run" button. The selected files will be deleted and copy ZIPped to catchme.zip located on desktop. Restart machine to complete operation.
Files to delete: c:\windows\system32\yruoykdhak.dat c:\windows\system32\yruoykdhak.exe c:\windows\system32\yruoykdhak_nav.dat c:\windows\system32\yruoykdhak_navps.dat
content of catchme.log
Processing "Files to delete:" file zipped: c:\windows\system32\yruoykdhak.dat -> catchme.zip -> yruoykdhak.dat ( 4761 bytes ) file "c:\windows\system32\yruoykdhak.dat" deleted successfully file zipped: c:\windows\system32\yruoykdhak.exe -> catchme.zip -> yruoykdhak.exe ( 336384 bytes ) file "c:\windows\system32\yruoykdhak.exe" deleted successfully file zipped: c:\windows\system32\yruoykdhak_nav.dat -> catchme.zip -> yruoykdhak_nav.dat ( 287805 bytes ) file "c:\windows\system32\yruoykdhak_nav.dat" deleted successfully file zipped: c:\windows\system32\yruoykdhak_navps.dat -> catchme.zip -> yruoykdhak_navps.dat ( 331 bytes ) file "c:\windows\system32\yruoykdhak_navps.dat" deleted successfully
How to destroy malware files
To destroy malicious executable files on the "Script" tab paste the list after "Files to kill:" command and click the "Run" button. The selected files will be destroyed and copy ZIPped to catchme.zip located on desktop. Restart machine to complete operation.
Files to kill: C:\WINDOWS\system32\drivers\symavc32.sys C:\WINDOWS\system32\drivers\Deg39.sys
content of catchme.log
Processing "Files to kill:" file zipped: C:\WINDOWS\system32\drivers\symavc32.sys -> catchme.zip -> symavc32.sys ( 178688 bytes ) PE file "C:\WINDOWS\system32\drivers\symavc32.sys" killed successfully file zipped: C:\WINDOWS\system32\drivers\Deg39.sys -> catchme.zip -> Deg39.sys ( 178688 bytes ) PE file "C:\WINDOWS\system32\drivers\Deg39.sys" killed successfully
How to collect files
To collect files paste the list on the "Script" tab after "Files:" command and click the "Run" button. The selected files will be ZIPped to catchme.zip located on desktop.
Files: C:\WINDOWS\system32\drivers\symavc32.sys C:\WINDOWS\system32\drivers\Deg39.sys
content of catchme.log
Processing "Files:" file zipped: C:\WINDOWS\system32\drivers\symavc32.sys -> catchme.zip -> symavc32.sys ( 178688 bytes ) file zipped: C:\WINDOWS\system32\drivers\Deg39.sys -> catchme.zip -> Deg39.sys ( 178688 bytes )
List of command line options recognized by catchme
to display all available options type: catchme -?
Usage: catchme.exe [options]
-p processes scan
-s servicess scan
-r autostart entries scan
-f [folder] files scan
-c source destination copy file
-e filename delete file
-E filename delete file without making a copy
-k filename kill file
-K filename kill file without making a copy
-o filename dummy overwrite/replace file with dummy
-O filename dummy overwrite/replace file with dummy without making a copy
-w filename str1 str2 replace unicode str1 with str2 in the file
-W filename str1 str2 replace unicode str1 with str2 in the file without making a copy
-m filename str1 str2 replace ascii str1 with str2 in the file
-M filename str1 str2 replace ascii str1 with str2 in the file without making a copy
-u do not display GUI
-a display all information
-t show all Alternate Data Streams
-g grab hidden files to %DESKTOP%\catchme.zip
-n use NTAPI
-d scan subfolders ( use with options -f and -a )
-l log file name
-I detect hidden items via catchme process
-q do not pause at end of scan
-h display this help
samples of usage:
catchme.exe -a -p
catchme.exe -a -s
catchme.exe -a -f C:\WINDOWS
catchme.exe -a -d -f C:\WINDOWS
catchme.exe -k C:\WINDOWS\system32:pe386.sys
catchme.exe -c C:\WINDOWS\system32:pe386.sys C:\pe386.sys
please note that you need administrator rights to perform deep scan
Example of using catchme - Trojan.Srizbi:
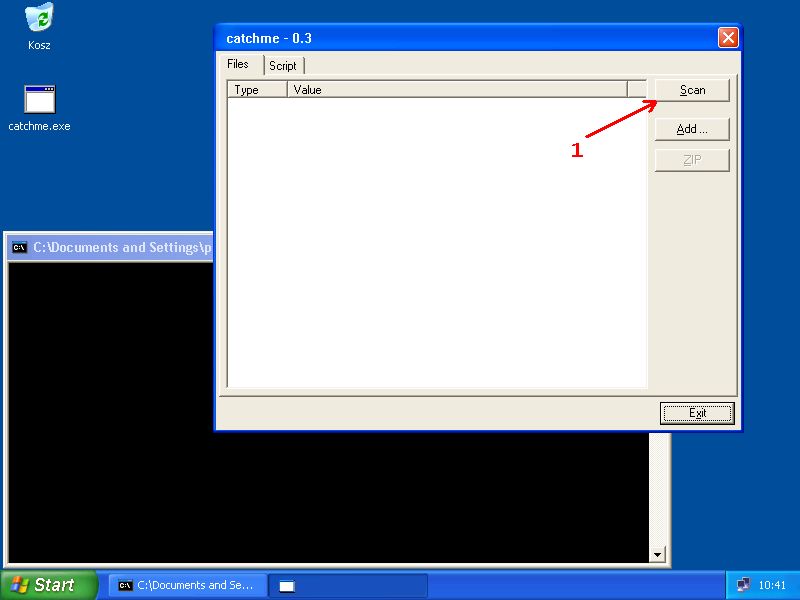
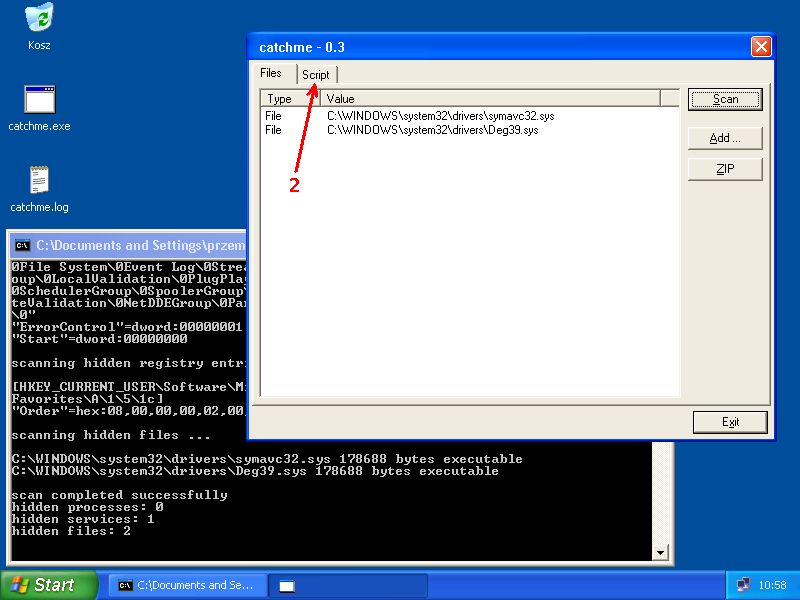
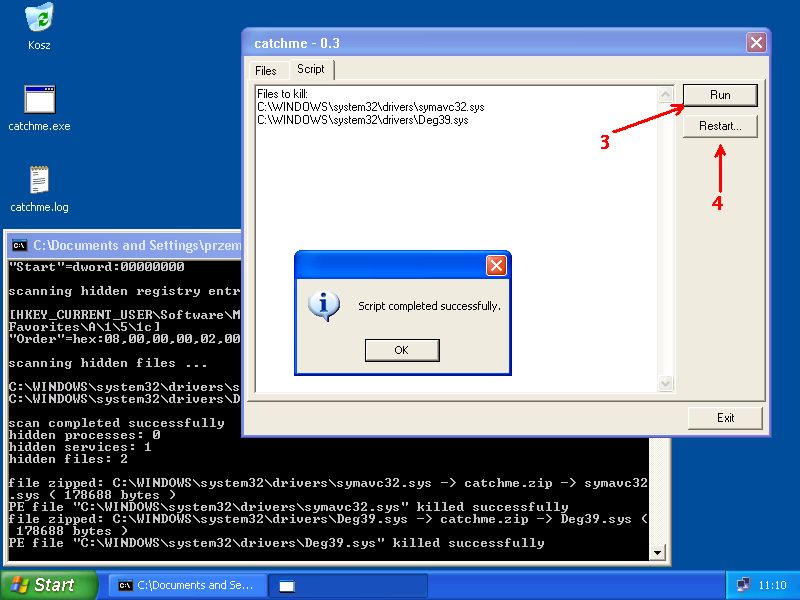
catchme 0.3.1262 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net Rootkit scan 2007-10-16 11:02:47 Windows 5.1.2600 Dodatek Service Pack 2 NTFS scanning hidden processes ... scanning hidden services & system hive ... [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Deg39] "Type"=dword:00000001 "Tag"=dword:00000001 "Group"="System Reserved\0Boot Bus Extender\0System Bus Extender\0SCSI miniport\0Port\0 Primary Disk\0SCSI Class\0SCSI CDROM Class\0FSFilter Infrastructure\0FSFilter System\0 FSFilter Bottom\0FSFilter Copy Protection\0FSFilter Security Enhancer\0FSFilter Open File\0 FSFilter Physical Quota Management\0FSFilter Encryption\0FSFilter Compression\0FSFilter HSM\0 FSFilter Cluster File System\0FSFilter System Recovery\0FSFilter Quota Management\0 FSFilter Content Screener\0FSFilter Continuous Backup\0FSFilter Replication\0 FSFilter Anti-Virus\0FSFilter Undelete\0FSFilter Activity Monitor\0FSFilter Top\0 Filter\0Boot File System\0Base\0Pointer Port\0Keyboard Port\0Pointer Class\0Keyboard Class\0 Video Init\0Video\0Video Save\0File System\0Event Log\0Streams Drivers\0NDIS Wrapper\0 COM Infrastructure\0UIGroup\0LocalValidation\0PlugPlay\0PNP_TDI\0NDIS\0TDI\0NetBIOSGroup\0 ShellSvcGroup\0SchedulerGroup\0SpoolerGroup\0AudioGroup\0SmartCardGroup\0NetworkProvider\0 RemoteValidation\0NetDDEGroup\0Parallel arbitrator\0Extended Base\0PCI Configuration\0" "ErrorControl"=dword:00000001 "Start"=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Services\Deg39] "Type"=dword:00000001 "Tag"=dword:00000001 "Group"="System Reserved\0Boot Bus Extender\0System Bus Extender\0SCSI miniport\0Port\0 Primary Disk\0SCSI Class\0SCSI CDROM Class\0FSFilter Infrastructure\0FSFilter System\0 FSFilter Bottom\0FSFilter Copy Protection\0FSFilter Security Enhancer\0FSFilter Open File\0 FSFilter Physical Quota Management\0FSFilter Encryption\0FSFilter Compression\0FSFilter HSM\0 FSFilter Cluster File System\0FSFilter System Recovery\0FSFilter Quota Management\0 FSFilter Content Screener\0FSFilter Continuous Backup\0FSFilter Replication\0 FSFilter Anti-Virus\0FSFilter Undelete\0FSFilter Activity Monitor\0FSFilter Top\0Filter\0 Boot File System\0Base\0Pointer Port\0Keyboard Port\0Pointer Class\0Keyboard Class\0 Video Init\0Video\0Video Save\0File System\0Event Log\0Streams Drivers\0NDIS Wrapper\0 COM Infrastructure\0UIGroup\0LocalValidation\0PlugPlay\0PNP_TDI\0NDIS\0TDI\0NetBIOSGroup\0 ShellSvcGroup\0SchedulerGroup\0SpoolerGroup\0AudioGroup\0SmartCardGroup\0NetworkProvider\0 RemoteValidation\0NetDDEGroup\0Parallel arbitrator\0Extended Base\0PCI Configuration\0" "ErrorControl"=dword:00000001 "Start"=dword:00000000 scanning hidden registry entries ... scanning hidden files ... C:\WINDOWS\system32\drivers\symavc32.sys 178688 bytes executable C:\WINDOWS\system32\drivers\Deg39.sys 178688 bytes executable scan completed successfully hidden processes: 0 hidden services: 1 hidden files: 2 file zipped: C:\WINDOWS\system32\drivers\symavc32.sys -> catchme.zip -> symavc32.sys ( 178688 bytes ) PE file "C:\WINDOWS\system32\drivers\symavc32.sys" killed successfully file zipped: C:\WINDOWS\system32\drivers\Deg39.sys -> catchme.zip -> Deg39.sys ( 178688 bytes ) PE file "C:\WINDOWS\system32\drivers\Deg39.sys" killed successfully
Previous version - catchme 0.2catchme 0.2 is the rootkit scanner that detects all userland rootkits including gromozon, hexdef, vanquish and AFX. It cannot detect kernel mode rootkits like Rustock ( PE386 ), Haxdoor, etc.
How to scan: Samples: |